OSForensics™ includes a built-in file viewer for analyzing the contents of files, deleted files, memory sections and raw sectors. The viewer consists of several modes that aids specifically with forensic data analysis.
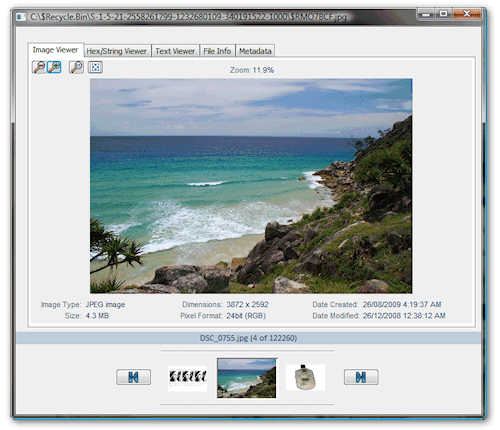
Image viewer
The image viewer attempts to view the data stream as an image. The following image formats are supported: BMP (Bitmap), JPG (JPEG), GIF, PNG, Exif and TIFF.
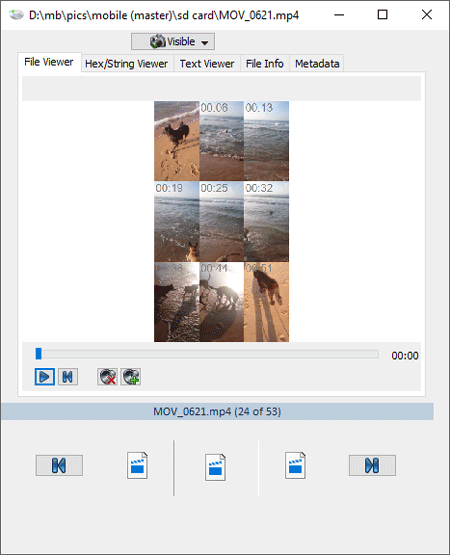
Video viewer
The video viewer plays video content and allows for quick inspection by displaying 9 still frames. The following image formats are supported: MPG, MPEG, MP4, AVI, MOV, M4V, MKV, OGV, WMV, RMV, RMVB, FLV, DIVX, and more.
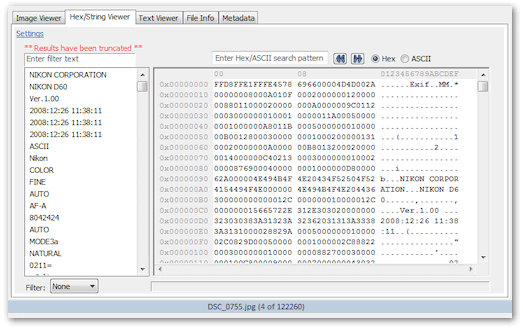
Hex/String Viewer (Binary String Extraction)
The hex/string viewer displays the data stream as raw bytes in hexadecimal. It can extract all ASCII/Unicode text strings contained in the stream (with user configurable string extraction settings specifying minimum and maximum string length, repeating character limit and more). You can also search within the Hex View and String List.
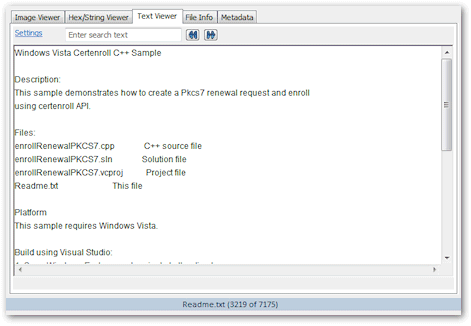
Text viewer
The text viewer displays the data stream as text. You can search within the text view. Note that any file format can be viewed as text, including binary files and image files. This can allow you to find hidden text within a binary file format. Of course, it is also used to view natural text file formats, such as .txt, readme files, and source code.
File information
Show the file attributes of the data stream: Location, Size, Size on disk, recognized file type, creation/modified/accessed dates, and any other file attributes (archive, compressed, read-only, system, hidden, symbolic link).
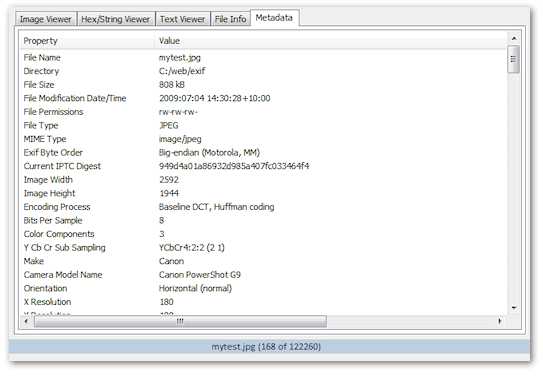
Meta data
Displays the meta data specific to the recognized file format. For image files, this would include Camera make, Model, etc. For documents, this would contain Author, Subject, etc.