File Decryption & Password Recovery
OSForensics supports file decryption and password recovery of Microsoft Office
documents (doc, docx, docm, xls, xlsx, xlsb, ppt, pps, pptx, pptm, ppsm),
archive files (zip, rar) and PDF files.

Depending on the type of encryption used (see the Document Encryption sections
for more information) OSForensics uses a different method to search for the
password, when 40bit encryption is being used each possible key is tested until
the correct one is found. For other types of encryption, a dictionary is used and
each word in the dictionary is tested against the file to check if it is the
unknown password.
Simply add a password protected file or files to the decryption queue. Once the files are chosen, select one or more available dictionaries from the list and click ‘Start’.

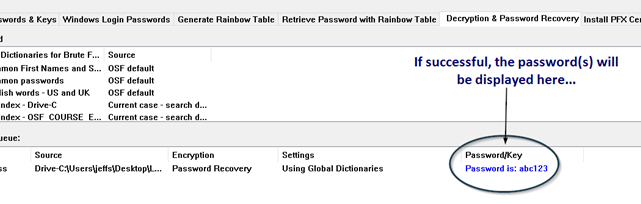
If successful, users will hear a short audio notification as OSForensics displayed the password as shown above.
For more information about password recovery in OSForensics see the sections below;
Document Encryption
Using a Case Search Dictionary
Adding a Custom Dictionary
Using the "Random" Dictionary
Distributed Password Recovery Clients (OSForensics Pro Edition Only)
Benchmarks
Troubleshooting
Document Encryption
In cryptography, a key is a bit stream of set length, eg 40bit,
128bit, 256bit (depending on the encryption method used) that is generated from
a password, which is an actual word or combination of
characters that is easily remembered by the user. If the encryption method
used is not very strong (such as 40bit encryption below) then the number of
possible keys is low, and each key can be tested until the correct one is found.
With stronger encryption methods this is no longer possible, and a dictionary of
words and phrases must be used in an attempt to find the correct password (also
known as a dictionary attack).
Microsoft Office documents versions 97 and 2000 used what is referred to as 40bit
encryption, using RC4 and MD5 algorithms where the key size was artificially
reduced to 40bits (to comply with US export regulations relating to
cryptography). This allows a brute force attack to test all possible key values
to decrypt the file, and can be completed in (at most) roughly 3 days of
testing.
Office XP and 2003 used a combination of 40bit and newer encryption methods
(SH1, 128bit RC4 keys and longer password lengths), so some files are able to be
decrypted using the above method while others will need to use dictionary
attacks to attempt decryption.
Office 2007 introduced a much more secure method of encrypting documents, using
AES and multiple hashing methods to further slow down the number of passwords
that can be tested (to approximately 200 a second).
RAR files use AES encryption and methods that slowdown the password testing
process, so only the dictionary based attack is possible. Older ZIP files used
their own proprietary algorithm which can be cracked in several hours if certain
criteria are met (needs to be a minimum number of files in the ZIP file). Newer
version of ZIP files can use AES encryption so only a dictionary attack can be
used.
PDF files can use 2 encryption methods, older ones (1.4 and
earlier) used 40bit
encryption, however newer version use larger keys (up to 256bit) and AES
encryption so only a dictionary attack can be used.
Using a Case Search Dictionary
If you have created a search index for your case you are able to use the dictionary of words generated as part of the password recovery process, any dictionaries detected for the current case will be added to the list of available dictionaries automatically. The image below has a dictionary named "My Index" which is from the current case.

These may be very useful and more likely to contain a password than the default dictionaries as the words are sourced from the hard disk under investigation. As many common passwords tend to be family names, pets, anniversary dates etc they may be (unintentionally) stored in emails and documents on the system.
Adding a Custom Dictionary
To add a custom dictionary a user simply needs to click on the Add Dictionary button…
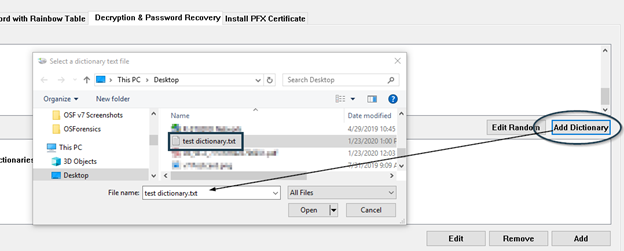
Your OSF dictionaries are stored in the following directory… C:\ProgramData\PassMark\OSForensics\PasswordRecovery\Dictionaries
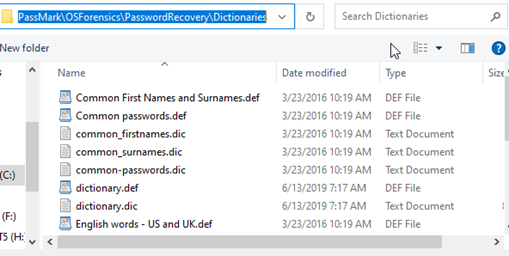
In windows Vista/Win7 this is C:\ProgramData\PassMark\OSForensics\PasswordRecovery\PDF. Once added to this folder your dictionary should appear in the list as seen in the image above, you will need to change to a different tab or section in OSForesnics to refresh this list after adding a new entry.
A dictionary file is simply a text file containing a list of words, one word per line, for example;
aardvark
aardvark's
aardvarks
aaron
More information and examples are given in the OSForensics Help file in the "Adding Dictionaries" section.
Using the Random Dictionary
Clicking the edit random button to the bottom right of the available dictionary list will open a dialog that allows you to choose a minimum and maximum password length as well as the character available for each particular character. This can be helpful if you know a portion of the password, such as the start or end character or when the character is not a dictionary word but a combination of letters, digits and symbols.
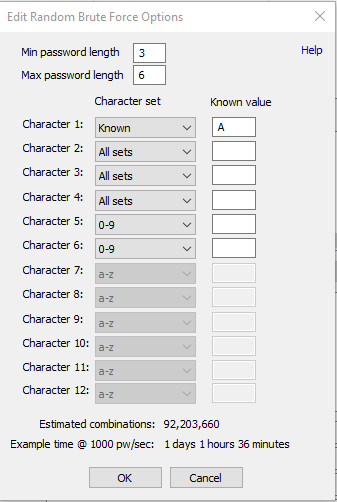
The image above will test password from 3 - 6 characters long, starting with "A", followed by up to 3 letters, symbols or numbers, and ending in up to 2 digits (For example, "A##", "A12z", "Abc#12" would all be generated by this option) and results in over 92 million passwords.
Be aware however that using this method becomes increasingly slower with each increase to the max number of characters in the password and/or the sets chosen for each character. For example, a 5 digit password of lower case letters (a-z) results in nearly 12 million (12,000,000) combinations and would take approximately 3 hours to test all the combinations on a fast CPU. If you were to keep the password length at 5 characters but expand the sets for each character to all available (upper case A-Z, lower case a-z, digits 0-9 and symbols) it would increase the number of combinations to more than 7 billion (7,000,000,000) and take nearly 85 days to test all the combinations.
Distributed Password Recovery Clients
Starting in OSForensics V9, the Professional Edition of OSForensics supports distributed password recovery. Using the external application, Password Recovery Client Manager (PWRecClientMgr.exe), on separate machines, users can run up to 1000 total clients when using the random password recovery to aid in the decryption of a file. See Setting up Distributed Password Recovery for more information.

Benchmarks
Benchmarks were performed using a system with a Core i5 2500K CPU and 8GB of DDR3 (1333MHz) RAM.
| Document Type | Speed |
| Microsoft Word 2010 | 633 passwords/sec |
| Microsoft Excel 2010 | 623 passwords/sec |
| Microsoft PowerPoint 2010 | 626 passwords/sec |
| PDF 128 bit AES/RC4 | 398,680 passwords/sec |
| PDF 256 bit AES | 4,687,446 passwords/sec |
| ZIP Standard | 11,906,533 password/sec |
| ZIP 128/256 bit | 19,791 passwords/sec |
| RAR | 174 passwords/sec |
| Microsoft Word 40 bit | 8 keys/sec |
| Microsoft Excel 40 bit | 8 keys/sec |
| PDF 40 bit | 32 keys/sec |
Troubleshooting
Server is unable to start
The password recovery module in OSForensics works by starting a server module
and several client modules (ones for each available processor). TCP/IP
connections are used for communication between the modules and as such they can
be blocked by firewall and internet security products (such as the Windows
firewall, Kaspersky and
AVG). If you are unable to start the server, please try disabling your
antivirus/firewall software while using the password recovery tools.
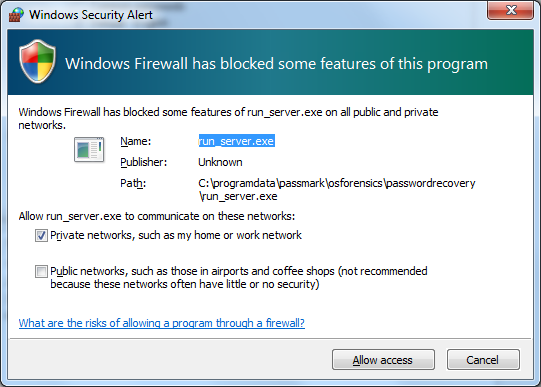
Windows Firewall
The Windows firewall may block the server
application and display the following alert, please allow run_server.exe to
communicate on "Private networks".
Videocard/GPU not being used but option enabled.
When decrypting a 40 bit file, use of GPU to decrypt is not currently supported. GPU decryption only applies for when the Random Passwords dictionary is being used. Also, note that not all GPUs are currently supported, e.g. older videocards or Intel GPUs.
Watch the below video for a tutorial on password recovery.
|
Password Recovery: See how to search for passwords stored in web browsers and retrieve passwords of encrypted documents (Note: The following video was created from an older version of OSForensics, but the topics covered still applies). Download Right-click to download, MP4 format, 9MB) |




