Identifying uninstalled software using Event Logs
Starting in V7, the Event Log Viewer in OSForensics can be used to help identify uninstalled software. Open the Event Log Viewer from the Start screen in OSF…
Like many other actions and events recorded within the Windows Event Logs you can analyze these logs for records of uninstalled software. Windows Event Logs are stored at the following path: C:\Windows\System32\winevt\Logs
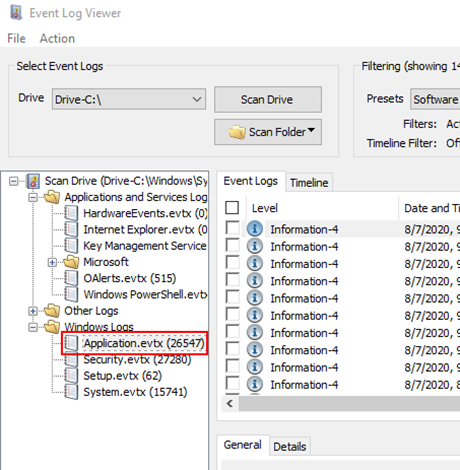
You will first need to run a scan to search for any Event Logs that are located on a forensic image file or connected drive. Once complete, navigate to the Application event logs as shown in this screenshot…
There will likely be tens of thousands of Application event logs on a system. To quickly identify logs that contain information about uninstalled software, use the Preset filtering options that are available in the drop-down menu…
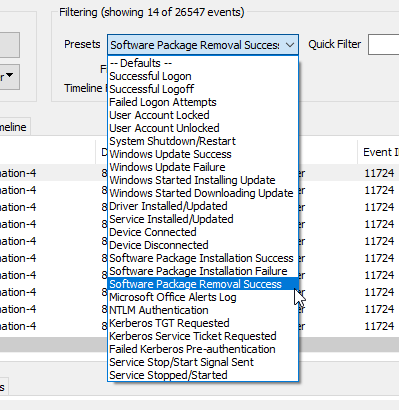
Choose the ‘Software Package Removal Success’ preset which will then filter and present you with all logs with Event ID 11724 that deal with software uninstallation.
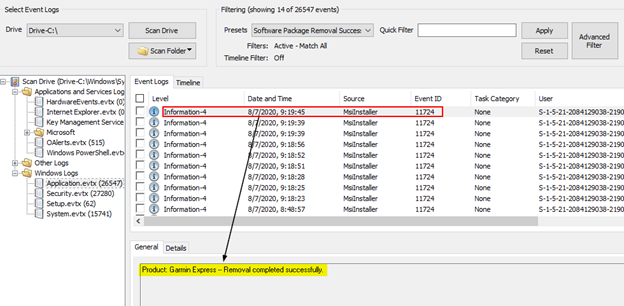
In the example above, we can see that the software application ‘Garmin Express’ was successfully uninstalled on 08/07/2020 at 09:19:45. Unfortunately, in our testing, this data is not comprehensive, meaning it does not seem to contain a complete historical list of uninstalled software.
Identifying uninstalled software through Shadow Copy comparison
Another way to search for and locate evidence of previously installed software is through Volume Shadow Copy analysis. OSForensics provides a fantastic tool to automate much of the heavy lifting with our Shadow Copy Analysis tool. Once you have added a forensic image or drive to your case in OSForensics, click on Add Device and choose the Volume Shadow Copy button. Any available Shadow Copies will be visible and available to be added to your case…

Once added to the case, you can then analysis any two of them to compare all similarities and differences using the Shadow Copy Analysis module…
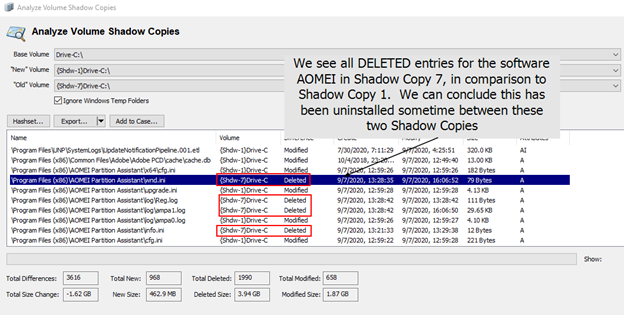
Simply point the tool to two different shadow copies and click the Analyze button. In about 30 seconds you’ll have a complete list of every file from both shadow copies. You can then export the results to a text file then use CTRL-F to quickly perform keyword searching. You can also use the various sorting capabilities sorting capabilities such as the ability to show all differences between both shadow copies…
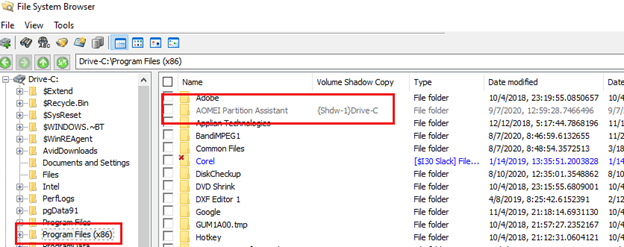
Checking the base volume (that contained the shadow copies), we can verify this software is no longer installed on this system yet in OSForensics File System Browser we still see it, though shaded, as it is still referenced in Shadow Copy 1…
Identifying uninstalled software using TOR (version 0.2.2.30) as an example
Most programs leave traces of information in the windows registry when it was previously run or installed on your hard drive. You can use the Create and Compare Signature function in OSForensics to search for a particular program that has been installed or previously installed.
In this tutorial, we will demonstrate how to search for the previously installed TOR Program. The procedure below documents a generalized way to identify file and registry artifacts that have been left behind as a result of applications being installed
Create a new signature of a clean Windows Virtual Machine
Step 1: Create a new virtual machine using VM Workstation. Follow the on screen wizard, select typical configuration. Create a new Windows 7 installation using either Window 7 installer disc or ISO image file. Once complete, power on the virtual machine which you have just created.
Step 2: Complete the Windows Update and then turn off the Window Automatic Update function. This is an important step before we start creating a new signature otherwise windows update will continuously run in the background. Install OSForensics and then download and install the Mozilla Firefox browser. Reboot the virtual machine.
Step 3: Create a new file signature of the clean Windows virtual machine, name this file "new_file.OSFsig".
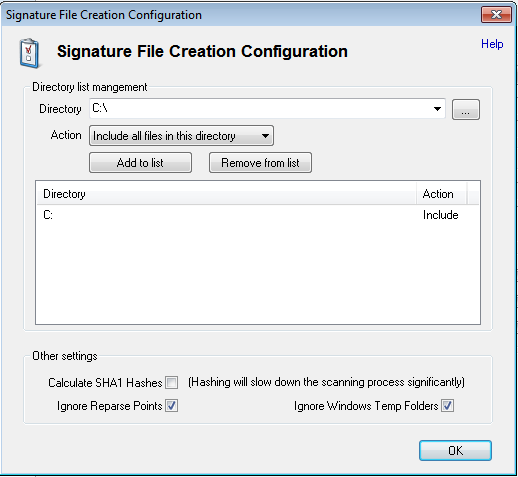
Step 4: Add the Registry Key options and remove the directory C:. Enable the Calculate SHA1 Hashes option. Create a new Registry signature of the clean Windows Virtual Machine, name this file "new_reg.OSFsig".
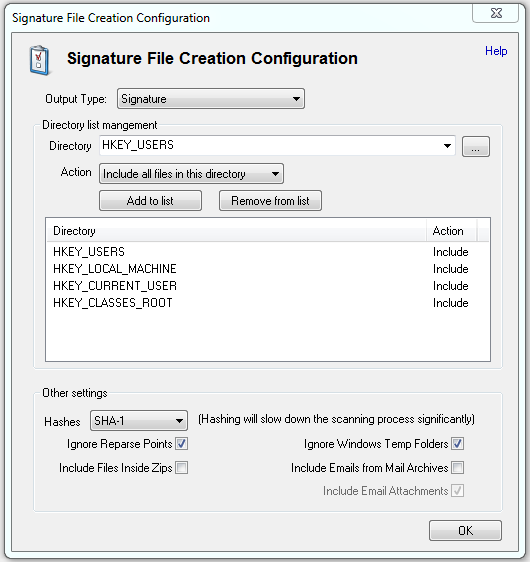
Create a signature of the Windows Virtual Machine with the Program installed
Step 5: Download the TOR program from the website http://www.torproject.org and install in the Windows Virtual Machine. Reboot the Virtual Machine again. Run TOR and make sure that FireFox is configured successfully.
Step 6: Create another File signature of the Windows Virtual Machine with the program installed, name this file "install_file.OSFsig".
Step 7: Create another Registry signature of the Windows Virtual Machines with the program installed, name this file "install_reg.OSFsig". Note: You need to turn on the hash set feature.
Create a signature of Windows Virtual Machine with the Program uninstalled
Step 8: Go to Control Panel and uninstall Tor from the Virtual Machine.
Step 9: Create another new File signature of the Windows Virtual Machines with the program uninstalled, name this file "uninstall_file.OSFsig".
Step 10: Create another new Registry signature of the Windows Virtual Machines with the program uninstalled, name this file "uninstall_reg.OSFsig". Note: You need to turn on the hash set feature.
Comparison of Signatures
Step 11: Compare the signatures of the "new_file.OSFsig"and "install_file.OSFsig" and "new_reg.OSFsig"and "install_reg.OSFsig". Look for specific program file difference and registry key differences.
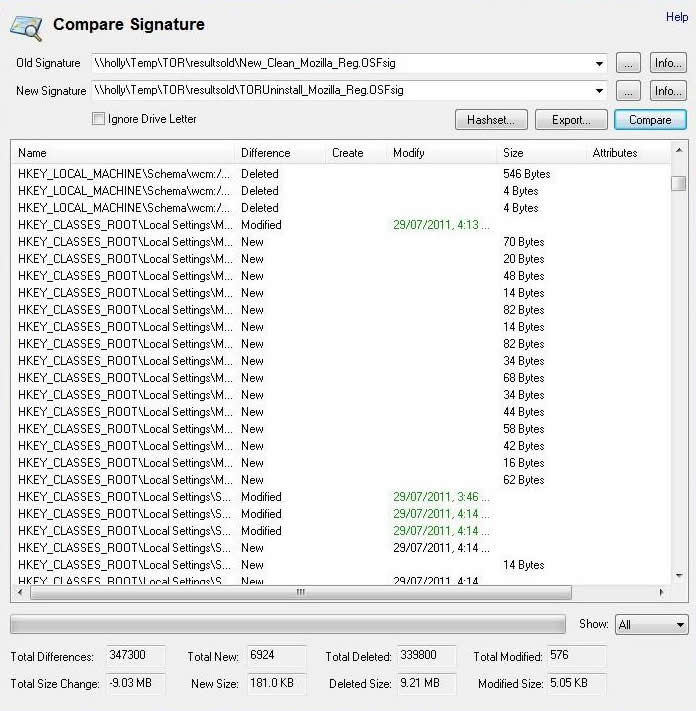
Step 12: Compare the signatures the "new_file.OSFsig"and "uninstall_file.OSFsig" and "new_reg.OSFsig"and "uninstall_reg.OSFsig". Look for specific program file difference and registry key differences.
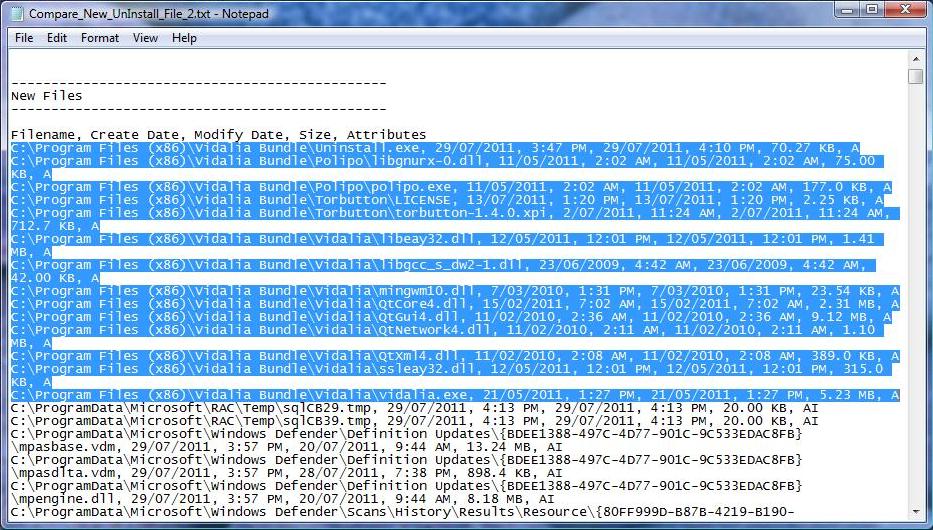
In the below example, we will search for the keyword "TOR" and "Vidalia" to identify traces of the installed and previously installed TOR program in the registry
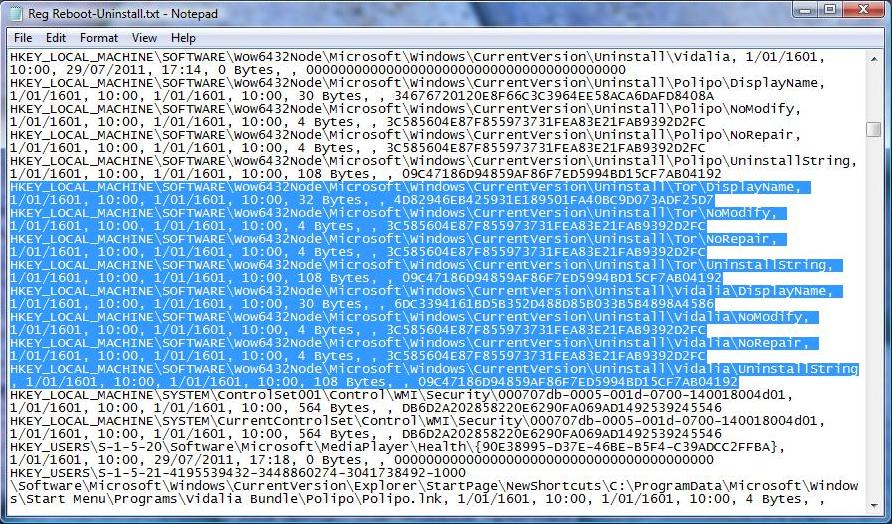
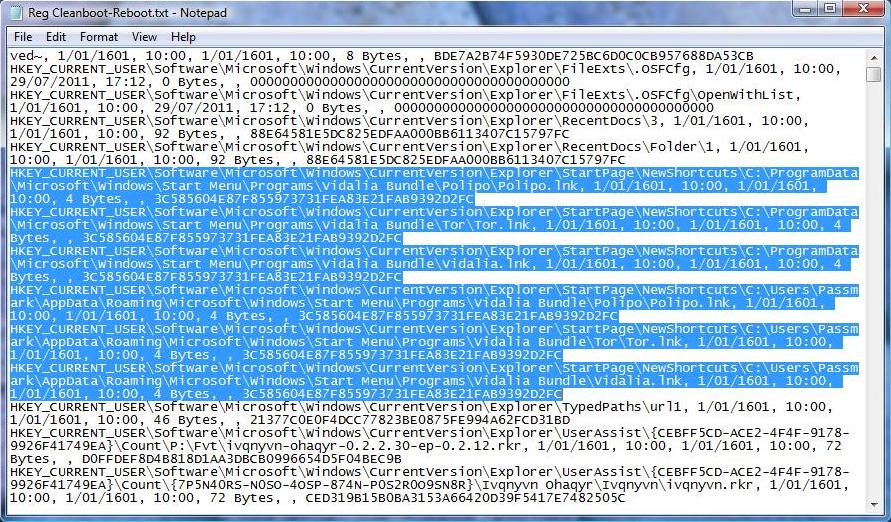
Results of the keyword search "TOR" and "Vidalia" to identify traces of the installed and previously installed TOR program in the file comparison.
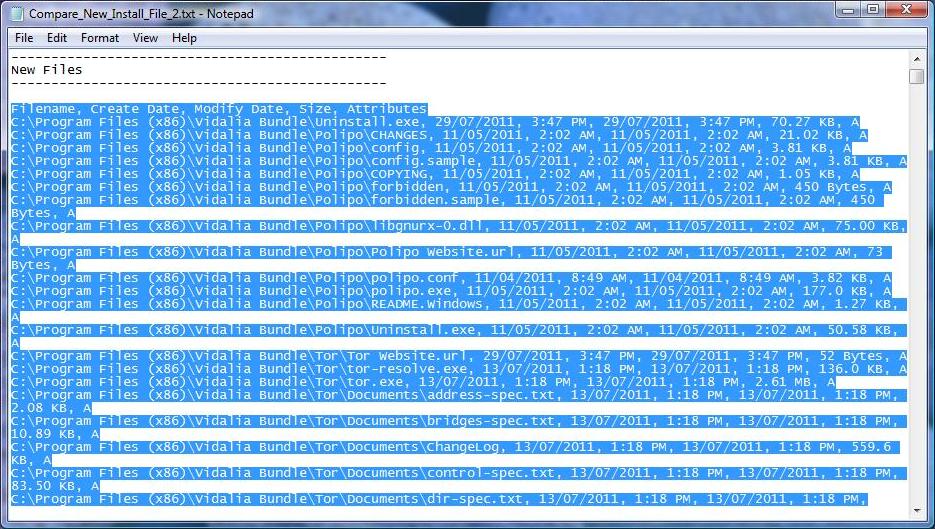
However be aware that if the program was run from a live CD or USB drive, which Tor does support, it will not leave traces like the examples above.




