How to Decrypt a BitLocker Drive
OSForensics is capable of accessing images or drives that are encrypted using Bitlocker, though it is important to understand that this is only achievable where the user has a valid key.
The following key protectors can be used to unlock a drive:
- Password
- Recovery Key
- Start-up Key File (.bek file)
-
The image or disk must first be added in its encrypted form to your case.
For example, an .E01 image file of a BitLocker encrypted drive, bitlocker.e01 is added under the ‘Image File’ option as shown in this example.
-
After the image is added, you need to then add the image again through the ‘BitLocker Encrypted Drive’ option.
-
To do this, open the ‘Add Device’ dialog and select ‘BitLocker Encrypted Drive’. From here you can select the previously added bitlocker.e01 image file from the drop-down list as it should already be pre-populated as shown below.
-
To do this, open the ‘Add Device’ dialog and select ‘BitLocker Encrypted Drive’. From here you can select the previously added bitlocker.e01 image file from the drop-down list as it should already be pre-populated as shown below.
- Click ‘OK’ which will open the BitLocker decryption window.
-
Select the appropriate key protector and enter corresponding key
-
If a Password is available, enter the password as shown below.
-
If a Recovery Key is available, enter the numerical key (as-is, including hyphens) shown below.
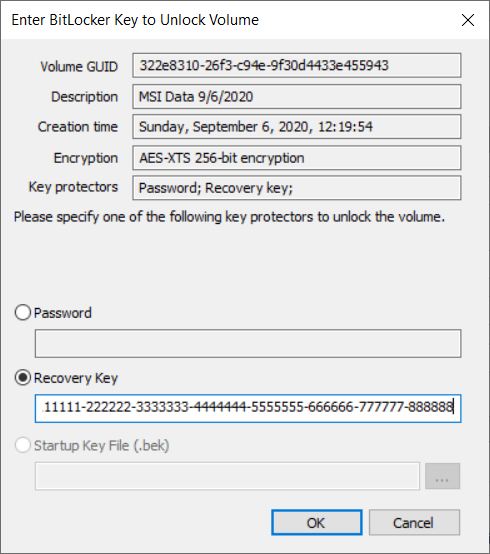
Note: the recovery key is completely numerical, not to be confused with the Identifier GUID (eg. 920ab36e-ae0f-4754-9b46-8796d1ac1e58)
-
If a Password is available, enter the password as shown below.
-
Once the key is verified, the image or disk is then added to the case.
Note: You will see both the encrypted disk and the decrypted disk listed under the ‘Devices’ category in the Manage Case module as shown below.
It is important to note that OSForensics supports the following encryption algorithms BitLocker uses to encrypt the drive:
- AES-CBC 128-bit encryption with diffuser
- AES-CBC 256-bit encryption with diffuser
- AES-CBC 128-bit encryption
- AES-CBC 256-bit encryption
- AES-XTS 128-bit encryption
- AES-XTS 256-bit encryption
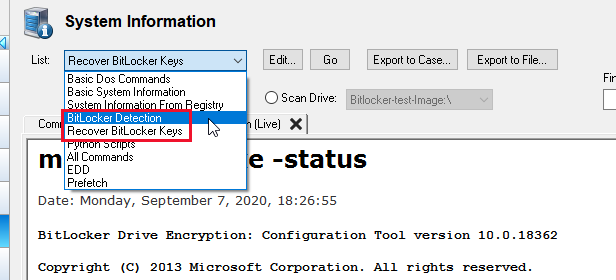
Detecting BitLocker:
On a live system, you can use an OSForensics USB to scan the system for the presence of any BitLocker protected drives or devices. If a BitLocker drive is found in an unlocked state, OSForensics can furthermore acquire and store the Recovery Key by utilizing a preset scan in the System Information module as shown below…