Using OSForensics with RegRipper
Before we provide an overview of how to integrate RegRipper, it is important to note that OSForensics has the ability to parse information through multiple modules such as Passwords, User Information and Deleted File Search.
However, if there is more obscure information which you which to retrieve from the registry, this can be done manually through the Registry Viewer in OSF and the 3rd part tool Reg Ripper at outlined below.
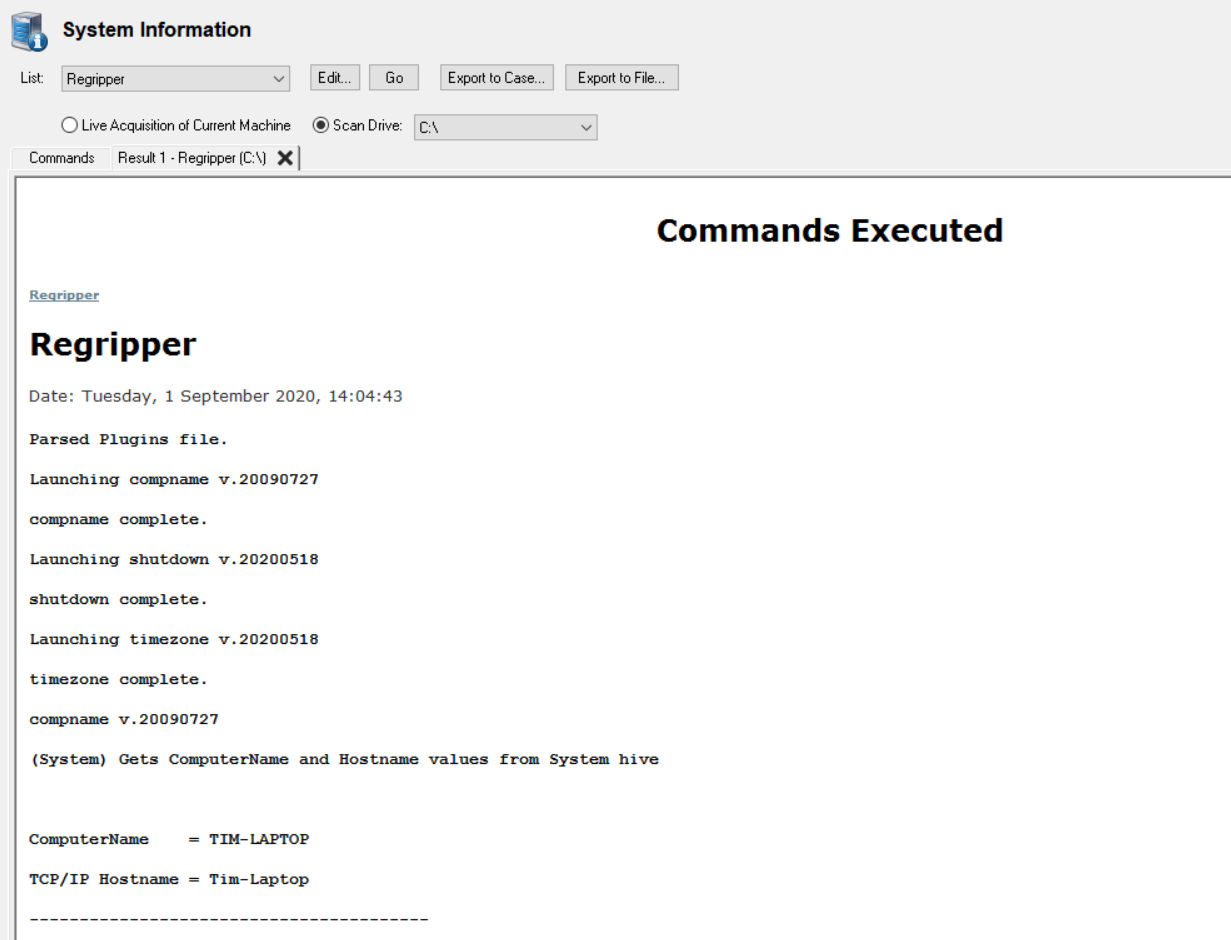
The System Information function in OSForensics allows external tools, such as RegRipper, to be called to retrieve information and save it to the case or export the information as a file. RegRipper is a well know tool used to extract information from the Windows registry hive files via perl scripts (plugins) that target specific areas of interest.
For this example we are using the compname.pl, shutdown.pl and timezone.pl
scripts in a
plugin file named "info" (seen below) to retrieve the computer name, last
shutdown time and timezone information from Windows\System32\config\SYSTEM
registry hive;
#-------------------------------------
#Retrieve the computer name, last shutdown time and timezone information from the registry
compname
shutdown
timezone
If the "info" file (no extension) is not in the plugins directory you can create it yourself though if the compname.pl, shutdown.pl or timezone.pl files are missing from the plugins directory this command won't run properly.
When downloading RegRipper, ensure the download includes all of the plugins. As this guide was written using RegRipper Version 3.0 (September 2020)
the plugins referenced may no longer be included in the regripper download.
After downloading RegRipper, if using Win10 copy the regripper folder into C:\ProgramData\PassMark\OSForensics\SysInfoTools\
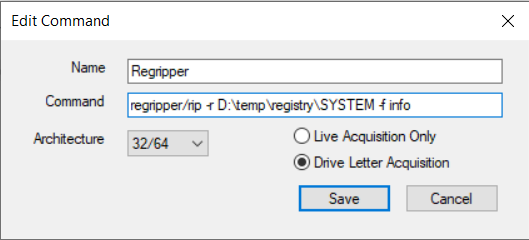
To add the command go to the System Information tab in OSF and click the Edit
button, then click the Add button to open the new command dialog.
In this example we are recovering data from the SYSTEM registry hive located on
drive D, so we will enter the command "regripper/rip -r D:\temp\registry\SYSTEM -f info".
Note that we are using the command line version of RegRipper (rip) that outputs
to stdout so OSForensics can read the output.
Highlight the newly added command and select the preferred list, you can add the command to one of the existing lists or create a new one to hold this and other RegRipper commands. Now click the "Add Selected" button to add the command to the list. Use the ok button to save the changes and close the dialog, you should now see the command listed in the System Information tab when you select the list.
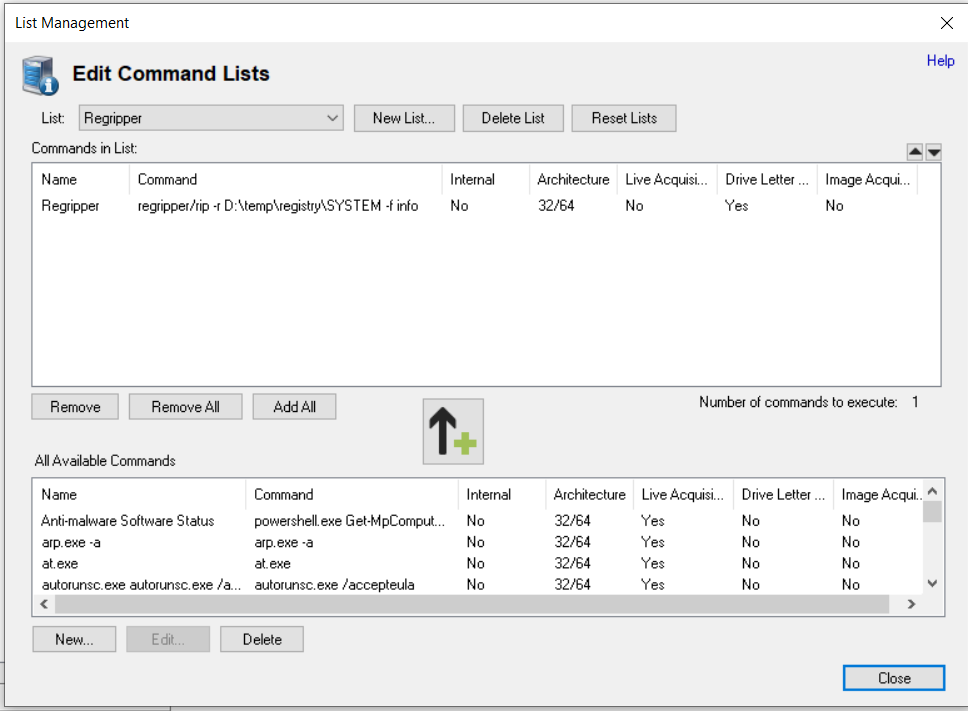
After running with the "Go" button the results will be displayed on the results tab and can be saved or exported as required.