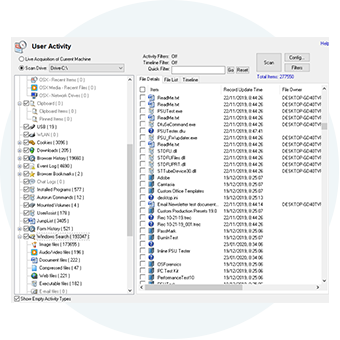
OSFMount
OSFMount allows you to mount local disk image files in Windows as a physical disk or a logical drive letter.

OSFClone
OSFClone enables you to create or clone exact raw disk images quickly and independent of the installed operating system.