Windows Login Password Recovery
OSForensics supports password recovery of Microsoft Windows user accounts by
using Rainbow Tables to compare hash values that are stored in the Windows
registry.
For more information about password recovery in OSForensics see the sections
below;
Recovering the Hash Values
Using Rainbow Tables
Recovering the Hash Values
Windows stores hash values for user passwords in the SAM registry hive. With access to the SAM and SYSTEM registry hives, OSForensics can recover the LM or NT hashes for the local Windows user accounts. To retrieve the hash values, go to the Windows Login Passwords tab in the Passwords section of OSForensics, select the appropriate device to scan and click the "Acquire Passwords" button. You should see a list of recovered usernames and hash values, and if you check the "Test common password" option you may see some simple passwords that were immediately cracked.
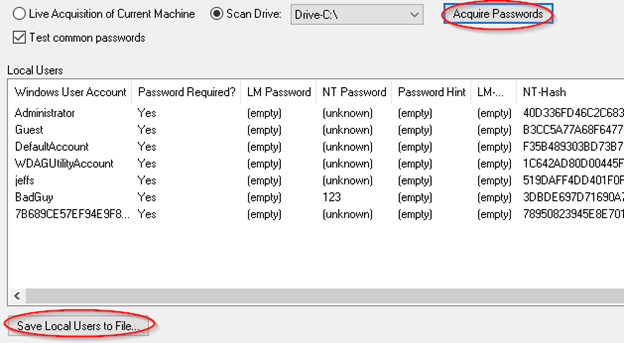
Once you have the hash values, click the "Save to File" button to save them as a
PWDUMP formatted text file. You can now use a rainbow table to process the file
and check for password matches.
Using Rainbow Tables
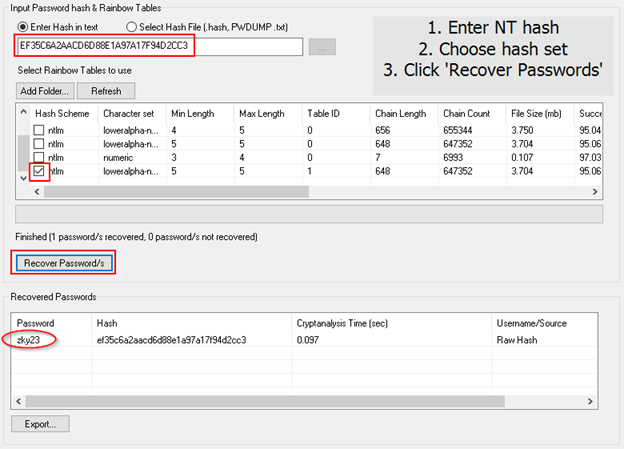
In the example below, I simply copied the NT hash value and pasted it into the hash box. I then chose an appropriate hash set and clicked ‘Recover Passwords’. OSForensics displayed the decrypted password in under a second.
Due to the way the LM hash values are generated, (although the passwords can be up to 14 characters long), the final hash value is actually a concatenation of two, 7 character password hashes, so the table only needs to be generated for a length of 1-7.
PassMark offers a large collection of Rainbow Tables and Hash Sets for purchase here.




